Cipherpunks
Digital Security Agency
World class technology and expertise
cyber security in defence and critical infrastrucure
future proof cyber security tools
Cyber security assessment and training
Solution example
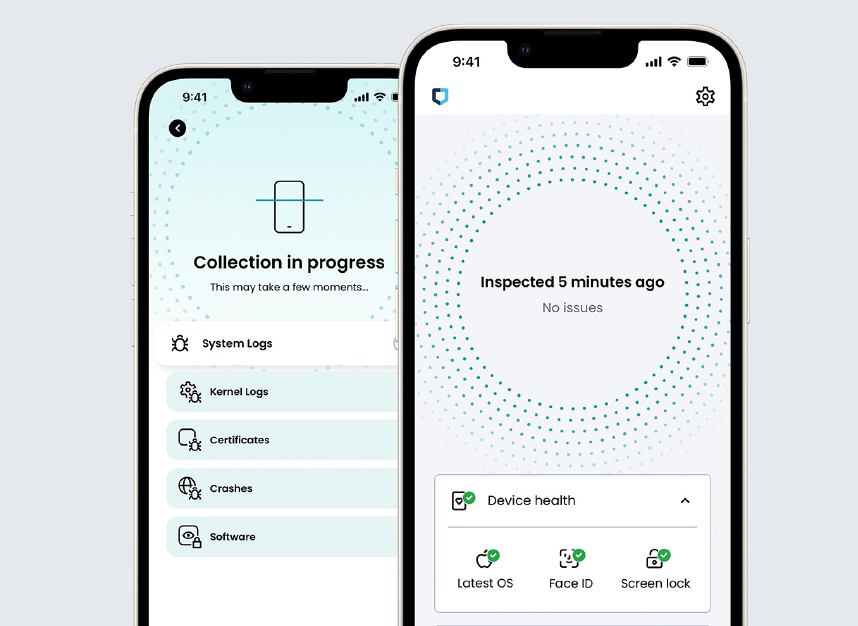
JAMF Executive Threat Protection is automated mobile phone forensics technology, which hunts and leverages attackers’ mistakes to discover immediatelly the breaches which no virus software can. System can detect advance governmental used malwares like NSO Pegasos and other remote and physical penetrations on mobile phones.
Technologies & Services
Technolgies
01 PASSWORDLESS AUTHENTICATION
Stolen and lost password are main reason why attackers are succesfull. Several services and organisations are deploying two-factor authentication solutiosn which include password and one-time-password or code which makes harder attackers to access accounts. Since attack methods have been developing this legacy 2FA does not create sufficient security for identities and accounts. Automated attacks are already in place which can bypass such legacy MFA solutions.
Ture passwordless authentication provides future proof identity and login protection which makes attacks against legacy MFA useless. Ask more from our Ciptor FIDO2 experts.
02 NETWORK SECURITY
Many data centers, industrial IT/OT networks, governmental confidential networks etc require more advanced network segmentation than traditional firewalls or virtual segementation can offer. With advanced Data Diode and ZoneGuard segementation solutions networks can be secured and data flows inspected with tools which are sertified to handle also up to EU SECRET level classified information. Ask more from our expers.
03 ADVANCED CRYPTOGRAPHY AND SECURE COMPUTING
In modern networks several intelligence and surveillance operations reveal the communication counterparties. End points like mobile phones and computers are vulnerable to malwares and spywares. Secure apps like WhatsApp are intercepted.
Securing business and operation classified data and conversations require more than standard COTS solutions. Cipherpunks solutions include advanced unbrakeable encryption technologies combined with hardened OS and secure computing environments for tailored purposes. Ask more from our experts.
04 SECURE COMMUNICATIONS SOLUTIONS
Conduct secure communications in public networks is a combination of purpose built systems and operational guidelinces. Our solutions include secure communication hardware devices and software for global and domestic scenarios. Systems are selected with based on customer needs and include OPSEC guidelines and purpose build comms solutions like hardened mobile devices and communitation applications. Read more from here >>
services
01 CYBER ASSESSEMENT AND STRATEGY CREATION In modern cyber environment digital processes and information flow is more and more vulnerable to several attack scenarios. With risk based evalutation model we can support organisations to identify relevant risks and create proactive models to imporve current defensive methods. New regulations like NIS2 and data protection related guidelines force companies and governmental agencies conduct more security measures which meet the requlations. Legacy tools are not providing sufficient cyber defense.
02 CYBER INTELLIGENCE AS SERVICE Many times being up to date with threats against your own organisation requires situational awareness in cyber domain. Company digital assests and and systems can be stolen and breached despite IT-team monitoring or SIEM system detections. Our solutions include deep and darkweb monitoring solutions to identify stolen assests and even attack planning against your organisaation. Also more sophisticated intercepting systems against criminals and counter intelligence are available based on legal use scenarios.
03 OPSEC AND CYBER HYGIENE TRAINING Cipherpunks tailor purose built training to improve the team or whole organisation cyber awareness and Opertational Security (OPSEC) to improve data loss risks. Best protection is combination of cyber hygiene training with suitable technological systems.
04 CYBER SECURITY CONSULTING We help in several level of cyber security related needs, wheather it is a cyber security measures in M&A process, Cyber security Due Dilligence or development project. Our expertise helps to identify risks in operations and conduct effective measures to mitigate risks.


